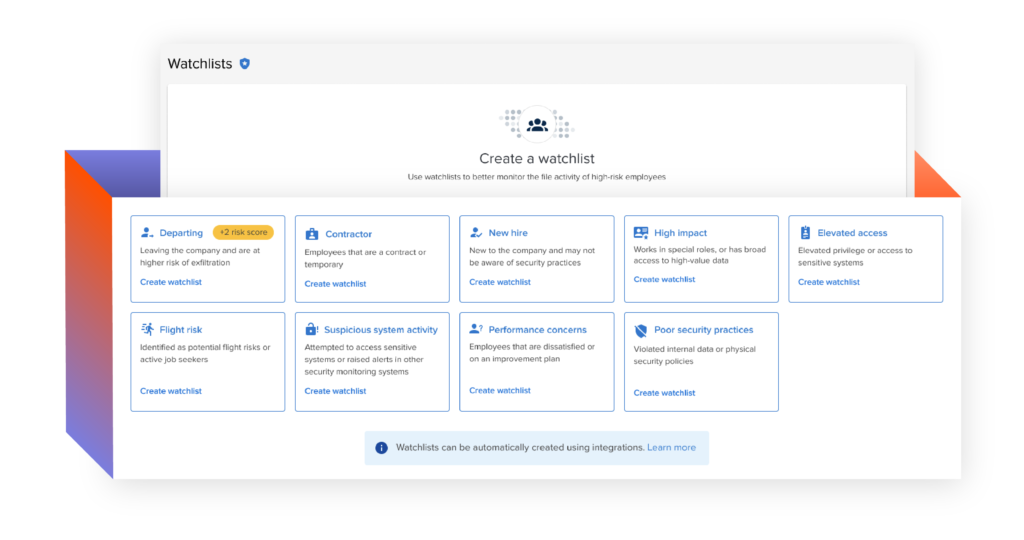
How it works
Add users to Watchlists to automate management workflows
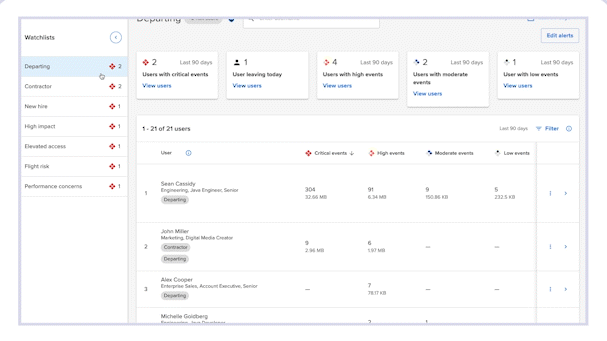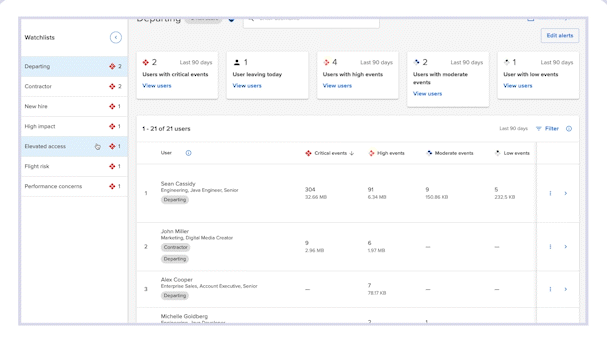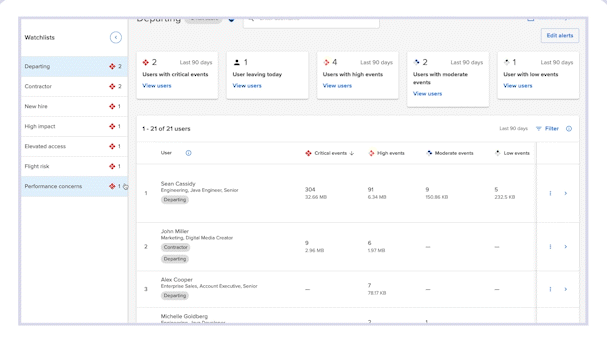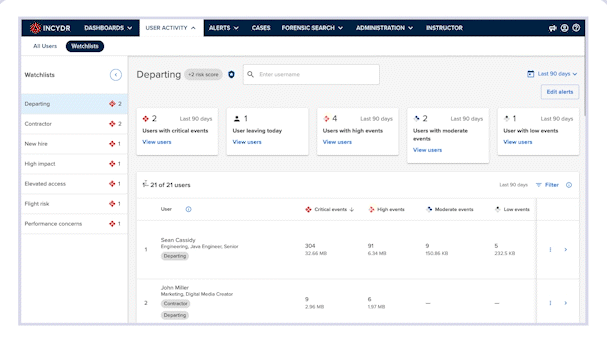
Adding users to a Watchlist kicks off system alerts and user management workflows so you can programmatically protect data when it is most vulnerable. Watchlists are commonly used for employees experiencing an employment milestone, such as departure, as well as those with risk factors that suggest the need for closer monitoring, such as contractors, new employees and those with privileged access.
- Focus and streamline management workflows
Drive a more efficient prioritization and investigation workflow by providing administrators with focused visualizations and alerts.
- Closely monitor high-risk users
Organize users of similar risk level into Watchlist groups based on their employment milestones, attributes and other risk factors.
- Automate processes and reduce error
Enhance monitoring by adding and removing users on Incydr Watchlists using directory groups or turnkey Incydr Flow automations with IAM, PAM and HRIS.
- Easily customize alert and blocking criteria
Create rules that are unique to user groups on specific Watchlists. Send prioritized alerts to your preferred system such as SIEM, ITSM, or Slack. Block file sharing for users on specified watchlists such as departing employee or repeat offenders.
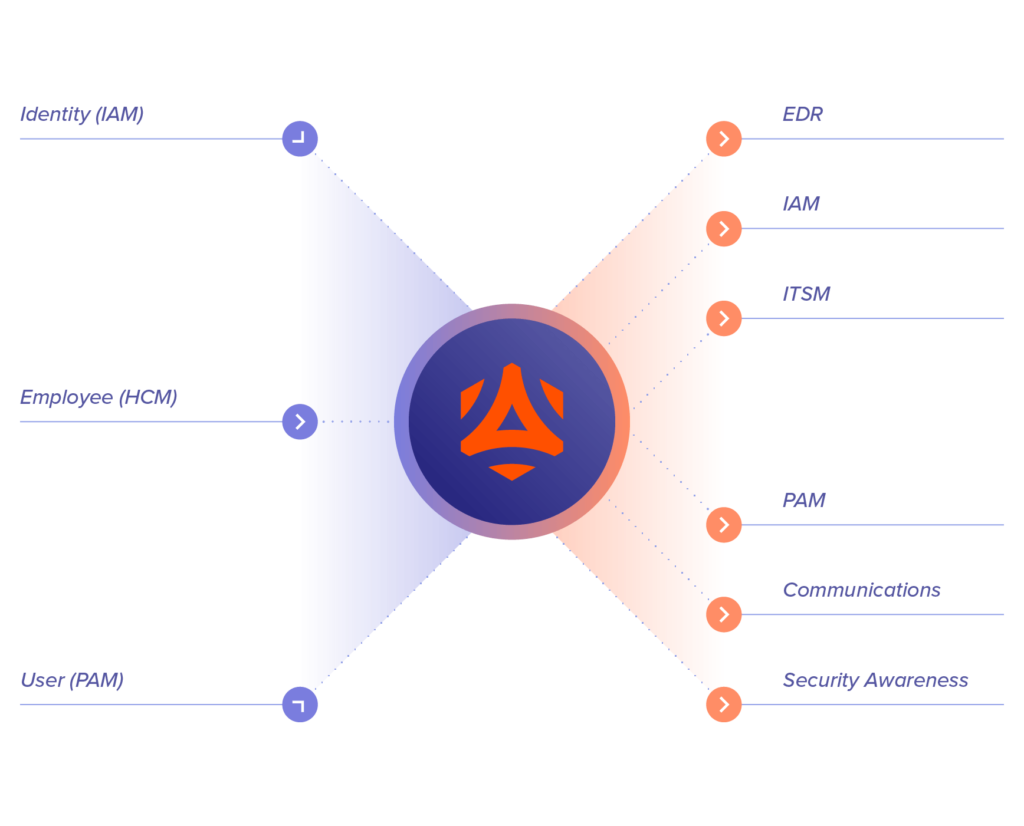
Use Incydr Flows™ to simplify Watchlist management
Incydr Flows enhance Incydr’s risk signal by automatically populating and managing your Watchlists. It does this by ingesting user attributes like employment milestones, departures, or elevated access credentials from corporate IAM, PAM, and HCM systems.
Learn MoreReady to see Watchlists in action?
Get a tour of how Incydr’s Watchlists make it easy to see and stop data leaks and IP theft – without violating employee privacy.
Connect With Sales
Dashboards
Customized insights that identify data exposure, training gaps, source code exfiltration, and corporate policy non-compliance. Dashboards measure overall program success across the organization.
Learn MorePRISM
Eliminate blindspots and focus on the threats that matter. PRISM is the system Incydr uses to prioritize and remediate both known and unknown data risks.
Learn MoreCases
Quickly document and retain investigation evidence for malicious and high-impact incidents, and create reports for key stakeholders such as management, HR and legal.
Learn More