Response Controls
Automated Response Controls That Don’t Burden Security Teams
Data risk isn’t black and white – it’s a spectrum. Security needs a way to manage the full spectrum of risk without disrupting employees or burdening analysts.
Code42 Incydr™ automates response to everyday mistakes, blocks the unacceptable, and frees up your time to investigate what’s unusual.
Connect With SalesOnly With Incydr
What does effective response to data risk look like?
Automatically send security training videos
Automatically send tailored micro-trainings to correct employee mistakes as they happen – driving down event volume and risk.
Access the content of exfiltrated files
Contain insider threats and speed investigations, with both integrated case management and access to file contents.
Block unacceptable data movement
Block unacceptable data movement without the management burden, inaccuracy, and endpoint impact of content-based policies.
Response Options
The right response control for every insider activity –
from mistake to threat
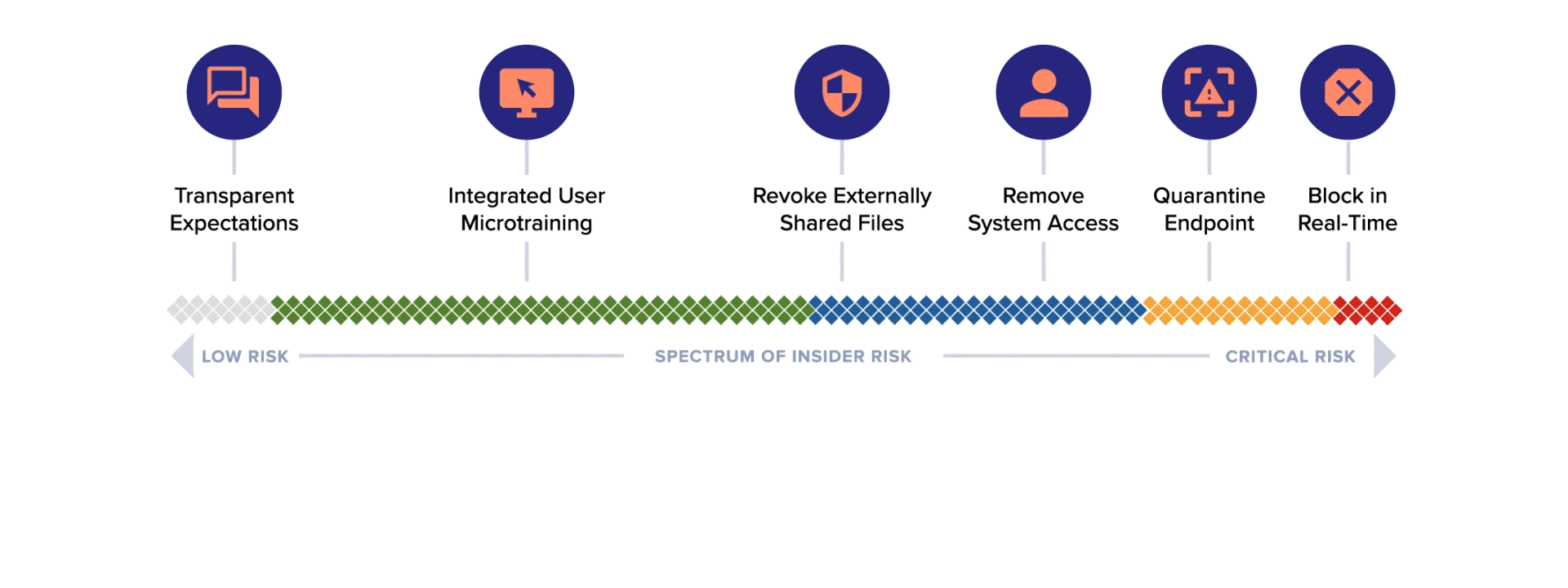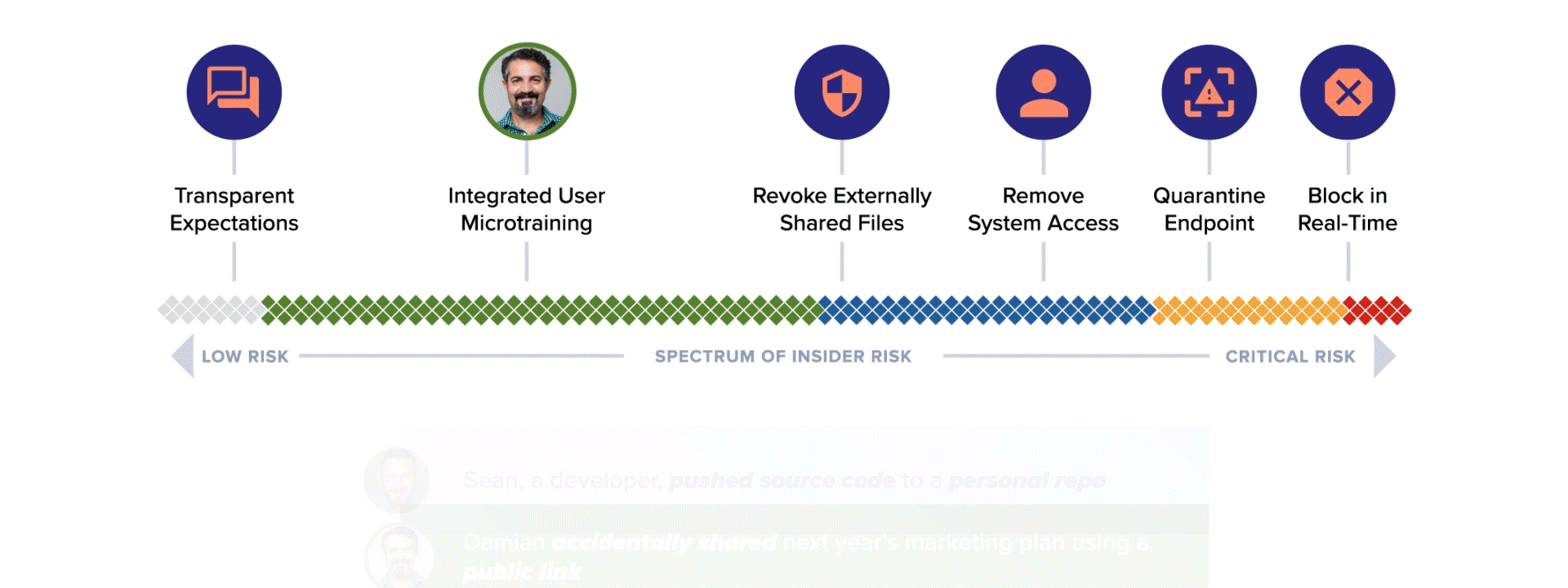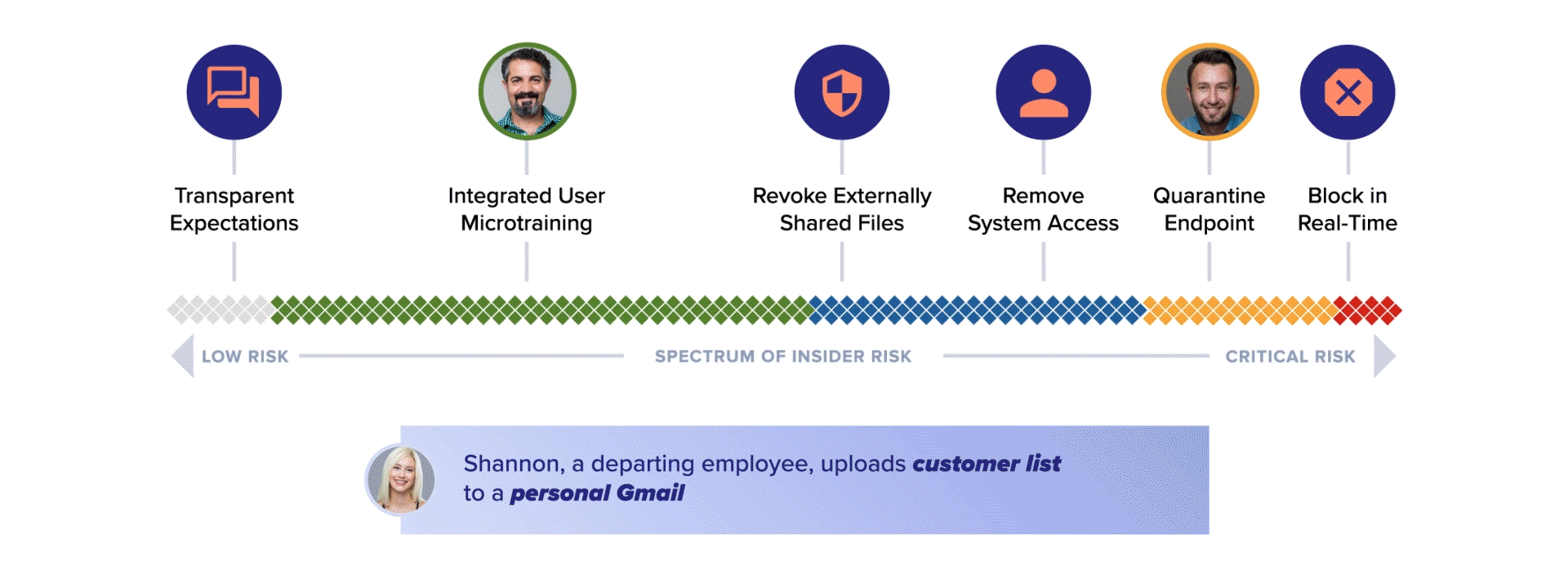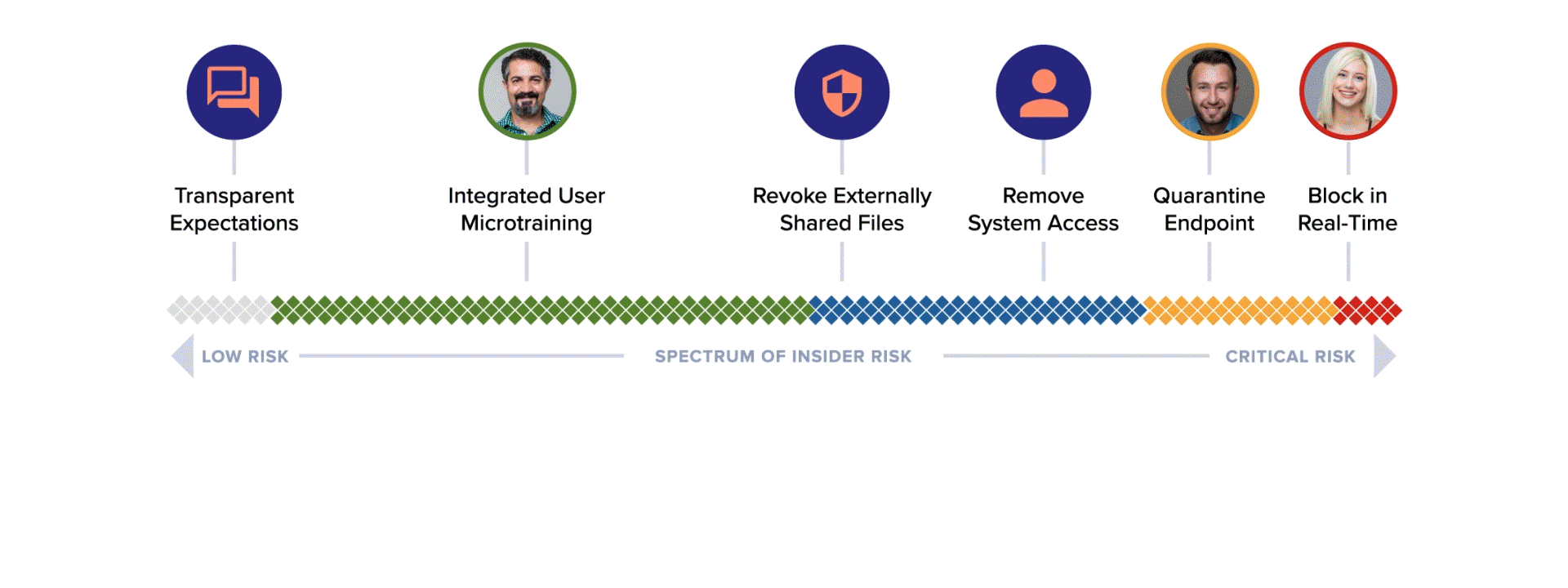
Transparent expectations
Establish expected employee security behaviors with communication and policy templates, role-based trainings and more.
Integrated user microtrainings
Correct employees when data is shared inappropriately using Code42 Instructor lessons that prevent risky activity from becoming the norm.
Real-time blocking
Prevent your highest-risk users from sending data to untrusted destinations.
Revoke externally shared files
Ensure insider threats aren’t able to damage the business by allowing security analysts to unshare files directly within Incydr.
Contain insider incidents and generate cases
Quarantine an endpoint or revoke system access while you conduct hands-on security investigation for risky behavior.
A response strategy that actually works
Learn more about response best practices and how Incydr can help you build a security-first culture with our white paper “How to build an effective, low-lift response strategy for Insider Risk.“
Download White Paper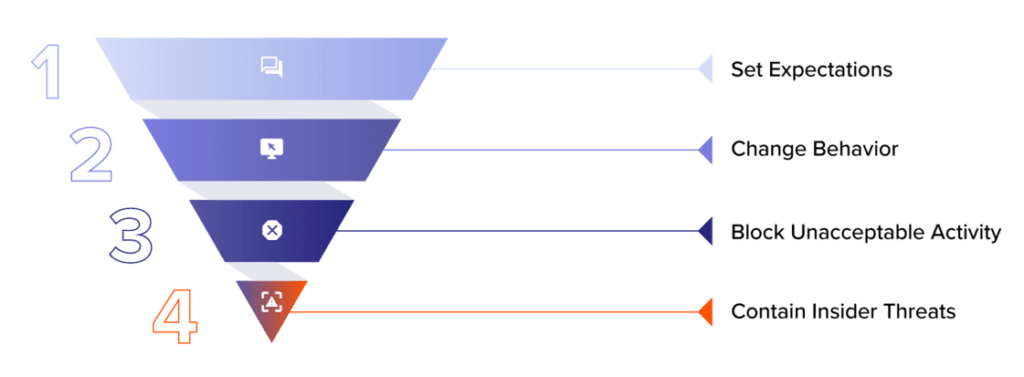
Want to see Response Controls in action?
Get a tour of how Incydr’s response controls make it easy to stop data leaks and IP theft without disrupting employee productivity.
Connect With SalesThere’s no response to data risk without detecting it first
Let’s not get ahead of ourselves – Incydr also offers complete visibility of data exposure and tools to investigate data incidents quickly.
Dashboards
Customized insights that identify data exposure, training gaps, source code exfiltration, and corporate policy non-compliance. Dashboards measure overall program success across the organization.
Learn MorePRISM
Eliminate blindspots and focus on the threats that matter. PRISM is the system Incydr uses to prioritize and remediate both known and unknown data risks.
Learn MoreForensic Search
Investigate event details and custom query a comprehensive, cloud-based index of activity metadata without putting strain on employee devices.
Learn More
Incydr helps avoid 19,000 hours of end user downtime over three years
According to the composite organization in Forrester TEI™ results.
Download Study