How it works
Query file activity in seconds
Forensic Search allows you to further investigate event details and custom query a comprehensive, cloud-based index of activity metadata without putting strain on employee devices. Incydr automatically populates the Forensic Search parameters required for insider threat investigations — and allows you to create your own custom searches based on the high-risk activity criteria you care about most.
- Review contextual metadata
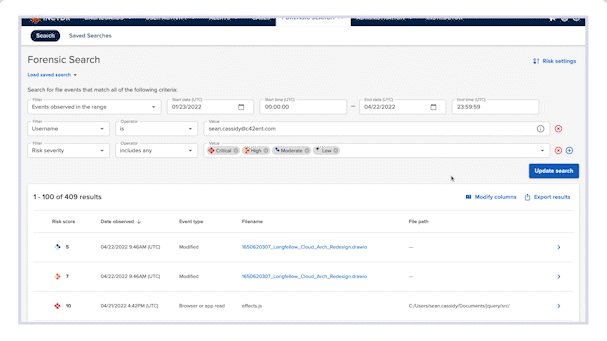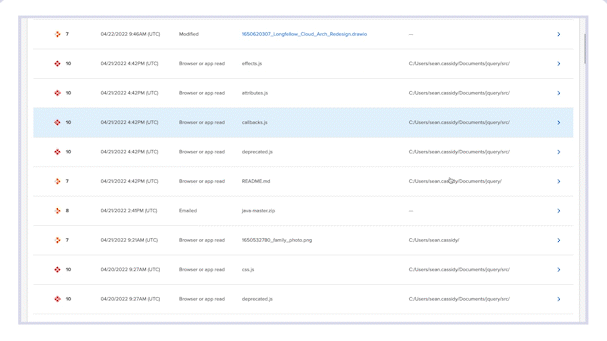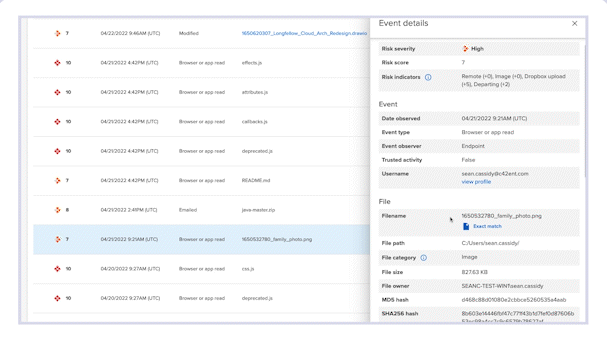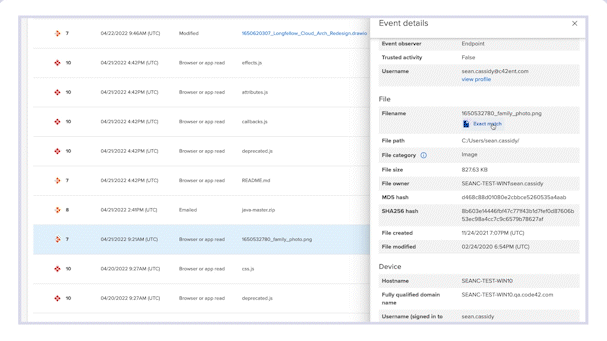
Forensic Search is the go-to place to review Incydr’s extensive set of metadata on event and file information.
- Access file contents
Authorized admins can view exfiltrated files to verify the value of contents and confirm they have not been obscured (i.e., File Mismatch IRI).
- Custom query in seconds
Easily query an organization-wide index of all metadata with no strain on endpoints. No physical device access needed for investigation.
- Run saved searches
Save and routinely run search queries for specific use cases, such as all exposure involving a specific file hash or all AirDrop activity for a set of users.
Incydr Metadata includes:
File Metadata
- File name, MD5 and SHA 256 hashes
- Owner, size, path, created and modified dates
- File category and MIP tags
Event Metadata
- Event date, time and type
- Source where the file event took place (computer, cloud, email)
- All Incydr Risk Indicators associated with the event
Device Metadata
- Hostname and FQDN
- The OS username for the person logged in to the device
- Private and public IP addresses
Destination Metadata
- Web browser active tab title and URL information
- Removable media make, model, volume name, partition ID and serial number
- Sync destinations and usernames
Want to see Forensic Search in action?
Get a tour of how Forensic Search makes it easy to detect and investigate data loss from insiders.
Connect With Sales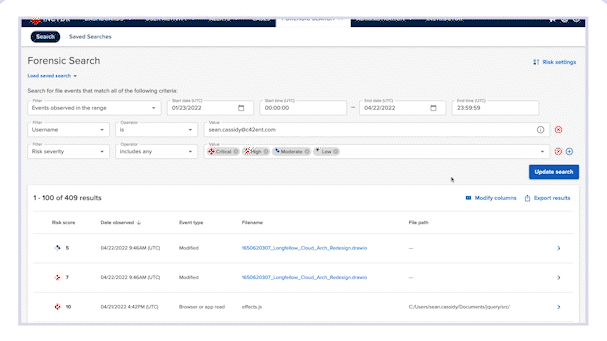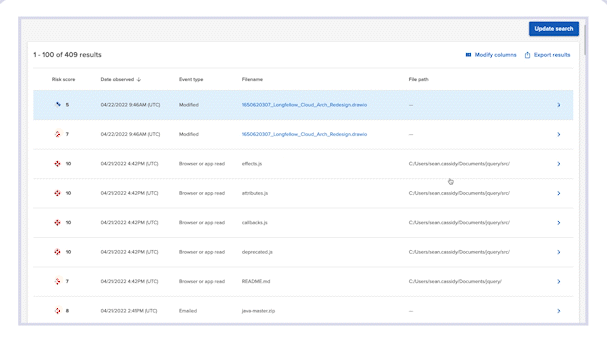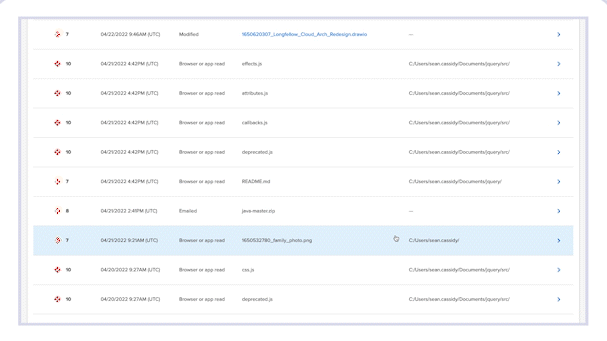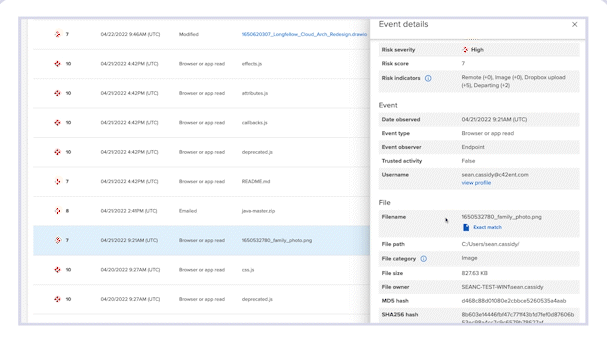
Dashboards
Customized insights that identify data exposure, training gaps, source code exfiltration, and corporate policy non-compliance. Dashboards measure overall program success across the organization.
Learn MorePRISM
Eliminate blindspots and focus on the threats that matter. PRISM is the system Incydr uses to prioritize and remediate both known and unknown data risks.
Learn MoreCases
Quickly document and retain investigation evidence for malicious and high-impact incidents, and create reports for key stakeholders such as management, HR and legal.
Learn More
Incydr can help reduce forensic investigation services on endpoint devices by 80%
According to the composite organization in Forrester TEI™ results.
Download Study