Change is scary, but necessary
Many organizations today are leveraging the Zero Trust security framework, but they forget that no-matter how much identity becomes the perimeter, people still need access to data to be able to do their jobs. Too often organizations ignore the value the of data that employees can access and the corresponding Insider Risk that access presents to the organization. Additionally, the COVID-19 pandemic magnified organizations’ Insider Risk as employees now access data via unmanaged networks and devices, often from their homes. Failing to recognize the larger business-continuity impacts that Insider Risk poses when valuable data is compromised leaves organizations vulnerable and exposed.
When we commissioned Forrester Consulting to conduct research on behalf of Code42 earlier this year, a key focus area for us was to understand how security practitioners are starting to think beyond the pandemic. For security, this essentially translates to “what does our strategy look like in a completely remote or hybrid work environment.” It is an understatement to say that security risks have changed drastically because of the pandemic. As I dug into the data more, it became clear that there has been a seismic shift. As an insightful DC villain once said, “There’s no going back. You’ve changed things forever!”
Download the full Forrester Paper on Cyber Security Predictions

My Top 5 Takeaways
While I think the research validated some of my assumptions, it had its share of surprises too! Here are my top takeaways from our research based on how companies are currently treating Insider Risk Management (IRM) and how strategies are adapting for the future.
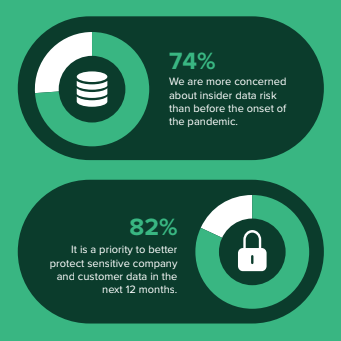
1. 74% of security decision makers are more concerned about Insider Risk than before the pandemic
No surprises on this one. Given the reality that workforces are remote, VPN tends to be an avoided 3-letter word, we have our own devices, and can essentially work any time we want we’re basically living the perfect recipe for increased Insider Risk. Thankfully, the top priority of 82% of security professionals is to better protect sensitive company and customer data. To tackle this, organizations are finding new approaches to protecting data, including protecting against internal breaches. Enter IRM!
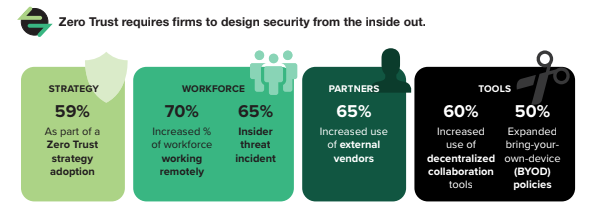
2. Zero Trust is driving the shift to Insider Risk Management, proactively!
The key word here is proactively. Insider Risk strategies are often a knee jerk reaction to a breach that has already occurred. A proactive and holistic approach to the problem has been overdue given the alarming increases we see in insider threat year over year. The adoption of Zero Trust, along with an increasingly remote workforce, insider threat incidents, and expanded use of third-party vendors, have pushed decision-makers to focus more heavily on IRM as the risks posed by insiders manifest in new ways through (and soon beyond) the pandemic.
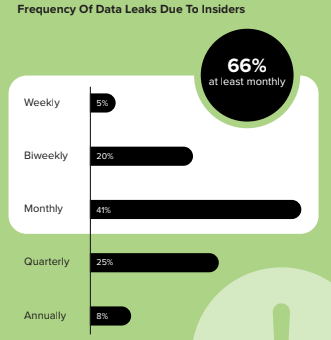
3. Data Leaks continue to happen because DLP strategies don’t work!
You’ve heard this from us before, but it’s worth reiterating. Many organizations continue to rely on legacy strategies and solutions to tackle this problem. 66% of respondents admit that they experience data leaks due to insiders at least monthly. On top of that, nearly three-quarters (71%) agree that the traditional approach to data leak prevention isn’t working, furthering the shift to a more holistic approach.
Put very bluntly; if Disney’s Elsa had any advice about DLP, it would clearly be as follows…

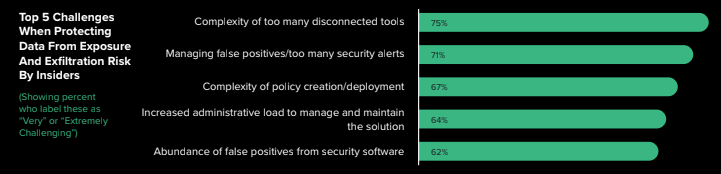
4. Tool And Policy Complexity Create Hurdles For Insider Risk Management
DLP strikes again! When asked what the challenges were when protecting data from exposure and exfiltration risk from insiders (Insider Risk), 71% cited managing too many false positives, and a close follower with 67% percent of the vote was the complexity of policy creation and deployment. The single largest concern was the fact that 75% of respondents said their tools just couldn’t even talk to each other. These hurdles greatly prohibit organizations’ Insider Risk efforts, exposing them to even greater risk while supposedly addressing it. Rather than making things worse with too many false positives and security alerts, a more holistic Insider Risk security approach as part of a Zero Trust strategy would shift companies from being reactive to threats to proactively identifying Insider Risks — thereby reducing complexity and driving down false positives.
5. The insider also happens to be your biggest security ally!
Face it, when we hear the term “insider” we have preconceived notions about this individual. We’re already thinking “this is a person that stole company data with malicious intent” because it’s the way we’ve been trained to think about the problem. We need to cut that out. Yesterday.
While technology is a big part of solving the Insider Risk problem, we cannot overlook the human side. Security awareness (as I noted in my previous blog: 10 Takeaways from Gartner 2020 Market Guide for Insider Risk Management Solutions) is emerging as a key investment area to mitigating Insider Risk. By turning our employees (the insiders) into security advocates, we empower them to become extensions of our security strategies. Rather than hindering, successful security programs embrace employees as security advocates to support safe data handling and computing use.

Download the Gartner 2020 Market Guide for Insider Risk Management Solutions
Insider Risk Management (IRM) will be an established category by the end of 2021 because…
- Insider Risk is hard to identify. Because risky insiders have trusted access and know their way around systems, they can be difficult to see and therefore time and attention needs to be paid to doing exactly that.
- Complexity — including disconnected tools (75%), false positives (71%), and complex policies (67%) — is the enemy. Security pros need processes for addressing insider risk that make it easy to operate and don’t allow risky insiders to flourish.
- Focus is key. A dedicated focus on Insider Risk helps recognize risky users before they cause harm.
- The status quo isn’t working!
- We won’t shut up about it until it is.
