You know the risks of insider threats and how they can leak valuable trade secrets, HR information, customer data and more — intentionally or not. But what’s the best way to prevent them?
It starts with understanding insider threat indicators.
In this guide, you’ll discover all you need to know about insider threat indicators so you can avoid data breaches and the potentially expensive fines, reputational damage and loss of competitive edge that come with them.
But first, it’s essential to cover a few basics.
What is an insider threat?
An insider threat is a cyber security risk that arises from someone with legitimate access to an organization’s data and systems. These individuals commonly include employees, interns, contractors, suppliers, partners and vendors.
While an insider with malicious intent might be the first situation to come to mind, not all insider threats operate this way.
Types of insider threats
Insider threats can cause many damaging situations, and they derive from two main types of individuals:
- Negligent insiders. These people unintentionally expose company information. They might treat security protocols like light guidance rather than strict rules or make an honest mistake while trying to adhere to security practices.
- Malicious insiders. Unlike negligent insiders, malicious insiders commit fraud deliberately. Their motivations may come from financial gain, vengeance or other personal reasons. Although malicious insider threats get more press, they don’t occur as frequently, with 78% of data breaches due to insiders being unintentional.
Regardless of their origin, insider threats can be tough to identify. To safeguard valuable data and protect intellectual property (IP), organizations should recognize the signs of insider threats.
Potential insider threat indicators
There are six common insider threat indicators, explained in detail below. While each may be benign on its own, a combination of them can increase the likelihood that an insider threat is occurring.
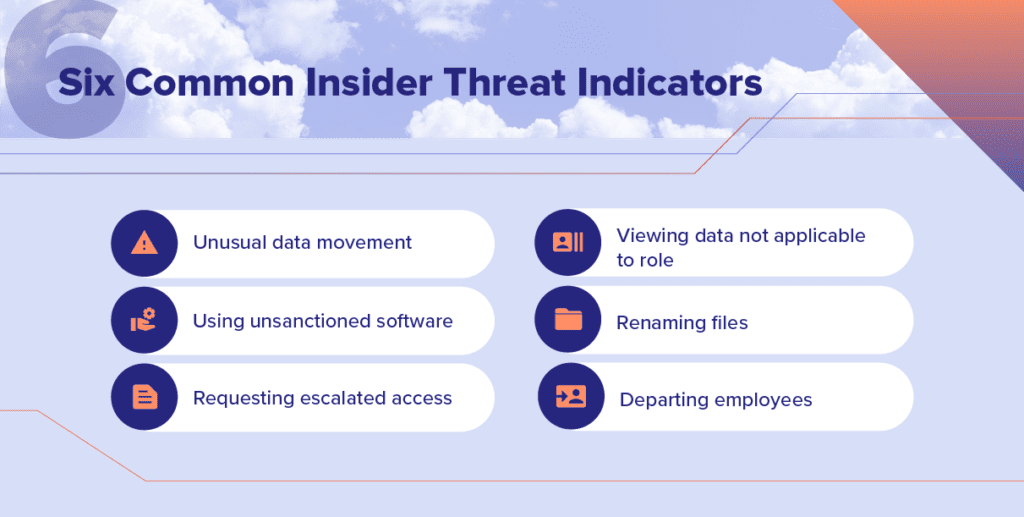
1. Unusual data movement
Excessive spikes in data downloads, sending large amounts of data outside the company and using Airdrop to transfer files can all be signs of an insider threat.
You may have tried labeling specific company data as sensitive or critical to catch these suspicious data movements. But even with the most robust data labeling policies and tools, intellectual property can slip through the cracks. It’s more effective to treat all data as potential IP and monitor file movements to untrusted devices and locations.
2. Use of unsanctioned software and hardware
Negligent and malicious insiders may install unapproved tools to streamline work or simplify data exfiltration. For instance, a project manager may sign up for an unauthorized application and use it to track the progress of an internal project. Malicious actors may install the ProtonMail extension to encrypt files they send to their personal email.
Regardless of intention, shadow IT may indicate an insider threat because unsanctioned software and hardware produce a gap in data security.
3. Increased requests for escalated privileges or permissions
It’s not unusual for employees, vendors or contractors to need permission to view sensitive information. It becomes a concern when an increasing number of people want access to it, as you have that many more potential risks to sensitive data.
For example, a malicious insider may want to harvest data they previously didn’t have access to so they could sell it on the dark web. In another situation, a negligent insider who accessed it from an unsecured network may accidentally leak the information and cause a data breach.
The more people with access to sensitive information, the more inherent insider threats you have on your hands.
4. Access to information that’s not core to their job function
Another potential signal of an insider threat is when someone views data not pertinent to their role. For instance, it would be suspicious if a marketing employee attempted to access their colleagues’ social security numbers since they don’t need this information to do their job.
While that example is explicit, other situations may not be so obvious. If an employee is working on a highly cross-functional project, accessing specific data that isn’t core to their job function may seem okay, even if they still don’t truly need it.
These situations, paired with other indicators, can help security teams uncover insider threats.
5. Renamed files where the file extension doesn’t match the content
Malicious insiders may try to mask their data exfiltration by renaming files.
For example, an employee who renames a PowerPoint file of a product roadmap to “2022 support tickets” is trying to hide its actual contents. Converting zip files to a JPEG extension is another example of concerning activity.
A data security tool that can find these mismatched files and extensions can help you detect potentially suspicious activity.
6. Departing employees
Whether an employee exits a company voluntarily or involuntarily, both scenarios can trigger insider threat activity.
Employees may forward strategic plans or templates to personal devices or storage systems to get a leg up in their next role. Others with more hostile intent may steal data and give it to competitors.
Departing employees is another reason why observing file movement from high-risk users instead of relying on data classification can help detect data leaks.
Why monitoring behavioral indicators alone is ineffective
Companies that only examine an employee’s physical behavior rather than a combination of the digital signals mentioned above may, unfortunately, miss an insider threat or misidentify the real reason an employee took data.
Some behavioral indicators include working at odd hours, frequently disputing with coworkers, having a sudden change in finances, declining in performance or missing work often. While these signals may indicate abnormal conduct, they’re not particularly reliable on their own for discovering insider threats. These signals could also mean changes in an employee’s personal life that a company may not be privy to.
Monitoring all file movements combined with user behavior gives security teams context. They can better identify patterns and respond to incidents according to their severity.
Strategies for insider threat prevention
Uncovering insider threats as they arise is crucial to avoid costly fines and reputational damage from data breaches.
Here are a few strategies you can implement to detect insider threat indicators and reduce the chances of a data leak:
- Implement access controls with a zero-trust strategy. A zero-trust strategy restricts employee permissions to those required for their role. Embracing zero trust decreases the damage insiders can do and makes any requests to upgrade their access more apparent.
- Use responsive security training. Long videos or training methods that employees will write off as a yearly “checklist item” may not drive secure work habits. Educating employees at multiple points throughout the year, especially after they make a mistake, can help them commit security best practices to memory.
- Monitor and protect all data, not just those you have classified as “important.” Monitoring all file movements can help protect data and prevent risky data behaviors from falling through the cracks — revealing insider threats before they leak data.
- Create a baseline of trusted activity. It’s easier to distinguish risky behavior from normal behavior with a benchmark. Optimal cyber security software can help you establish which devices and destinations you trust and identify suspicious data movements to places you don’t.
- Start an insider threat program. Even if you have a limited budget, the long-term benefit of creating a robust insider threat program will be worth the resources and hassle you’ll save by proactively addressing the risk of insider threats.
Using one or a combination of these tactics to detect insider threats can help streamline your security team’s workflow and prevent insider threats from happening.
Start detecting insider threat indicators
One seemingly harmless move by a negligent contractor or malicious theft by a disgruntled employee can jeopardize your company’s data and IP. These situations can lead to financial or reputational damage as well as a loss of competitive edge.
Security leaders can start detecting insider threat indicators before damage occurs by implementing strategies for insider threat prevention — including using software that monitors for data exfiltration from insiders.
One such detection software is Incydr. Incydr tracks all data movement to untrusted locations like USB drives, personal emails, web browsers and more. Its automated risk prioritization model gives security teams complete visibility into suspicious (and not suspicious!) data exfiltrations. The solution also has a wide range of response controls to minimize insider threat data leaks and encourages secure work habits from employees in the future.
Take action against insider threat indicators
Code42 Incydr helps you quickly see and stop data leak and theft by employees in one platform – eliminating the need for DLP, CASB, and UEBA.
