In September’s Incydr Scoop, we told you about the growing problem that is Insider Risk, and began to quantify its prevalence as illustrated by product telemetry data generated by Incydr. Insider Risk is a data protection problem resulting from when employees accidentally or intentionally expose, leak or mishandle data. From October to November, the percent of file activity which exposed data grew by 60%.
As Insider Risk continues to grow and evolve, Incydr customers have the intelligence they need to correlate file, vector and user characteristics and behavior, to surface insider risk indicators (IRIs). IRIs inform security teams which data events pose the greatest risk to their organization, so that they can investigate and respond accordingly. At an aggregate level, here is a picture of the Insider Risks security teams have mitigated in November 2020.
The data exposure breakdown
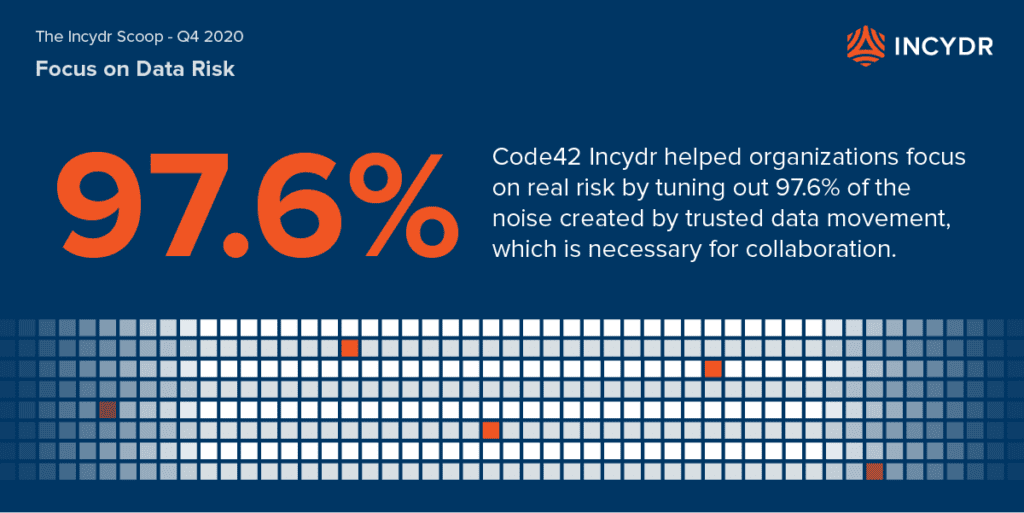
Data exposure is caused by a variety of Insider Risk sources, such as when data is synced to unauthorized cloud storage, personal email uploads to cloud apps via web browsers, sent through AirDrop or messaging platforms like Slack. In the month of November, a total of 144M file exposure events occurred across 185K endpoints. While this is a significant number, it is only 2.4% of the total file events (files created, modified, deleted, shared to trusted domains) that occurred in the month. By tuning out 97.6% of the noise created by trusted data movement, which is necessary for collaboration, Incydr enables customers to focus on real risk.
Most Exposed File Type: Business documents
Ignorance is bliss, they say, except when it comes to a data security strategy. It is crucial to understand exactly what data is exposed – that is the pinnacle to managing Insider Risk. If your workforce is anything like our customers, you can expect that on average an employee exposed 22 files per day in the month of November. The specific file types that were exposed most often during November included:
- 33% business documents
- 5% source code
- 4% zip files
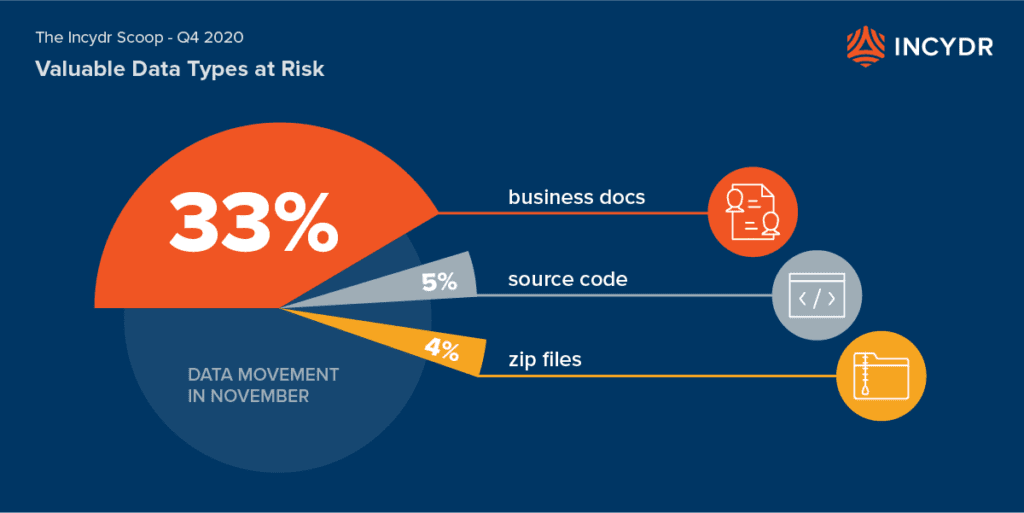
Even though business docs seem innocuous enough, they can hold incredibly important data, like passwords, customer lists, IP, etc. Rather than being ignorant to the data exposure and file contents, Incydr customers have the visibility needed to investigate and respond appropriately for the level of Insider Risk assessed.
Top Data Exfiltration Vectors: Removable media and cloud services
It’s easier than ever to create data, and the avenues it can be shared—or exposed—are growing by the minute. Email and removable media remain common sources of data exfiltration, but the cloud era has opened the door to countless cloud services, browsers and other applications like AirDrop, WhatsApp, Slack, WeChat and more. While the exposure vectors are vast, the most pervasive exfiltration vectors identified in the month of November were:
- 50% removable media, up significantly from 33% in October
- 41% synced to a cloud service
- 6% read by browser or other application
- 2% shared outside of trusted domains
- 1% links were made publicly available in the cloud
Just hearing the scale of the Insider Risk problem can be overwhelming. As organizations innovate, share data and collaborate across a distributed user base, it’s more crucial than ever to balance the constant movement of data with effective data risk detection and response.
Key Insider Risk Indicators: Prioritize events for investigation and cut out noise
Alert fatigue is real and risk is relative, so having the ability to prioritize the specific events that bring the greatest risk to an organization today is more crucial than ever. IRIs are Incydr’s method for prioritizing risks that demand remediation first. Here is a look at a few of our IRIs:
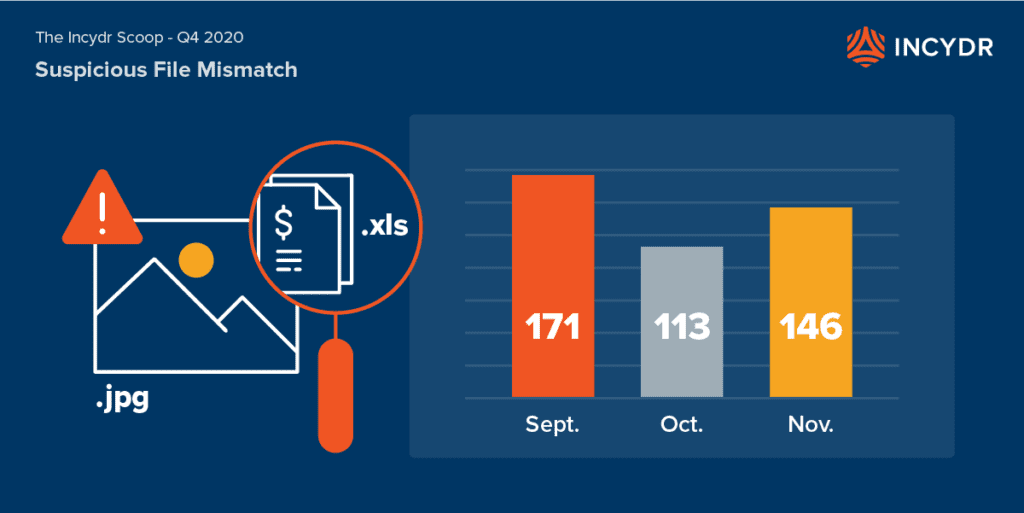
Suspicious File Mismatch is when an exposed file, which has the MIME type of a high-value file, such as a spreadsheet, is disguised as a low-value file type, like a JPEG. This sequence is highly indicative of malicious intent and occurred more frequently in recent months than it had previously been reported (Q3: Incydr Scoop).
Off hours is when Incydr identifies endpoint file activity that occurs outside of when a specific employee is typically active on their computer. Incydr identified more off hours file exposure events on Monday, November 23, than any other day in the month. More than half (54%) of all file exposure events that day occurred off hours.
When employees depart an organization, it represents a significant milestone in the employment lifecycle, and is a particularly noteworthy IRI. Incydr customers prioritize and automate risk remediation of departing employees through the use of risk detection lenses. On average, 62 departing employee cases were opened each day in November across Incydr’s customer base. Customers in the manufacturing and technology industry experienced a higher number of departing employees than those in other industries.
Total departing employee cases opened by industry:
- Manufacturing: 1,292 cases
- Technology: 260 cases
- Professional services: 46 cases
- Media & Entertainment: 46 cases
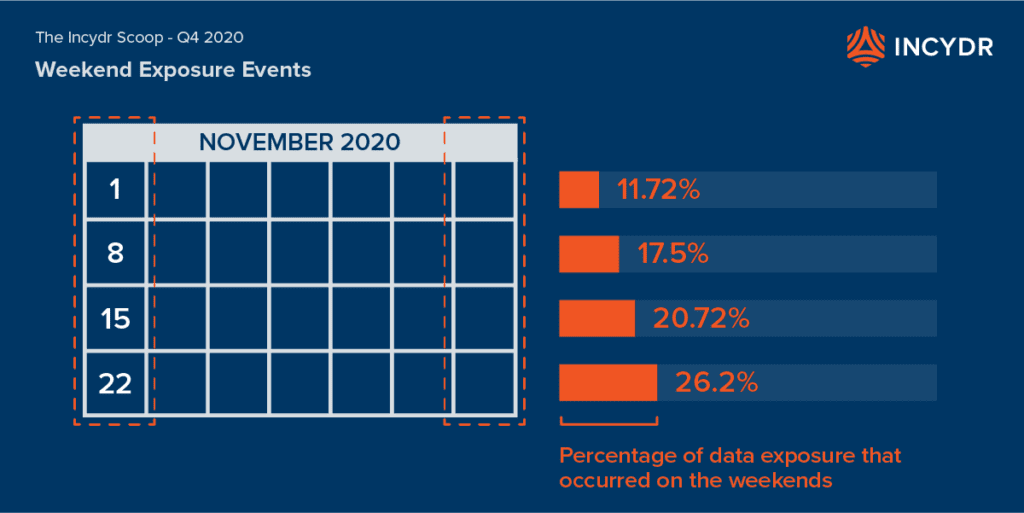
Weekend file exposures take off in November
Data exposure occurs every day, which is why it is crucial to have a system that manages Insider Risk by identifying, prioritizing and remediating IRIs. That said, looking at the trend over the past three months, on average 17.8% of data exposure occurred on the weekends. This percentage gradually increased in November, reaching a new high around the Thanksgiving holiday.
Thanks for tuning in to this quarter’s Incydr Scoop. We will be back with an update on these product-driven insights in Q1 2021. Until then, learn more about how you can use Incydr to gain the data risk intelligence you need to better manage your own Insider Risk.
Get more insights about insider risk in in the latest Data Exposure Report.
