Digital business transformation requires a fast-moving, collaborative culture. As companies on this fast track focus on innovation and speed to market, they inherently introduce more risk from the inside. Furthermore, in 2020, remote work became the norm, requiring increased adoption of cloud collaboration technologies. This shift caused a sudden acceleration of insider risk like we’ve never seen before.
Employees are being onboarded, enabled, empowered and offboarded, all in a remote world. On top of that, they’re downloading, uploading, emailing, AirDropping, messaging, posting, syncing, sharing, dragging and dropping corporate data 24/7—largely from their company-issued laptop. The upside is that these tools make them more productive. The downside is that these same tools make it easier to exfiltrate data.
Code42 Incydr app for Sumo Logic
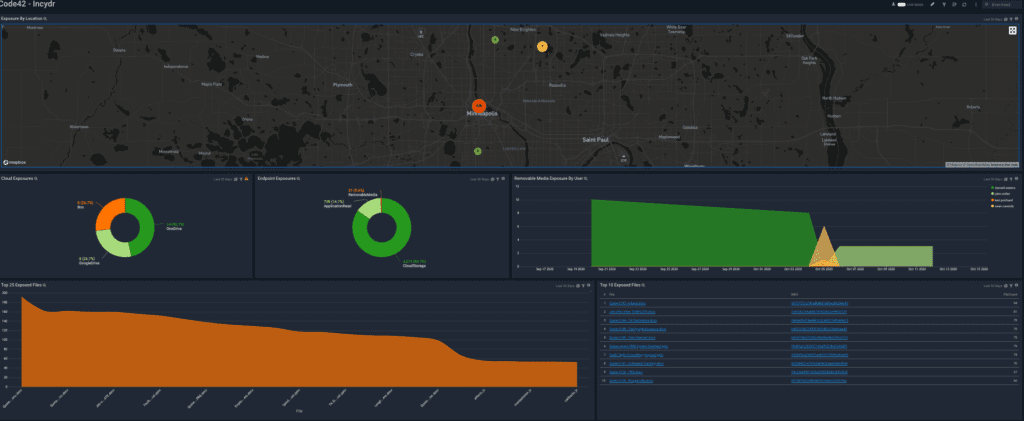
The new Code42 Incydr app for Sumo Logic allows security teams to monitor file movement and sharing across computers, cloud and email to provide an accurate picture of insider risk vulnerabilities. Teams can configure Incydr’s file exposure and exfiltration events into existing Sumo Logic dashboards, or create custom dashboards within Sumo Logic Cloud SIEM to easily visualize:
- Cloud and endpoint data exposure events
- Removable media exposure by user
- Exposure by filename
- Top files exposed
- Top endpoint and cloud users by exposure type
- Exposure events by location
How it works
Incydr detects when data is put at risk by observing all employee file activity that takes place on computers and within corporate cloud and email services. By continuously monitoring all file activity – including activities like uploading files to web browsers, web apps, syncing files to personal cloud apps, and transferring files to removable media devices – Incydr takes a multidimensional approach to insider risk by combining rich context on files, vectors and users.
Custom dashboards within Sumo Logic Cloud SIEM provide a single, centralized view of activity indicative of insider risk. From this view, security teams can drill into specific geographical regions, users, and exposure types – and for file activity requiring further investigation, teams can quickly view file-level details by MD5 hash, directly from within Sumo Logic to make fast, informed decisions on how to respond, whether that be automated action, corrective conversation, additional training or even legal action.
Getting started
The best news? Getting started is easy. The Code42 Incydr app is available in the Sumo Logic Marketplace, and as part of the open source community, it’s easy for joint customers to propose new features, identify new use cases, and contribute to ongoing app improvements aligned with partners’ feature enhancements and resolution of issues.
Not using Code42 Incydr today? Deployment takes as little as 48 hours, so you can quickly make a positive impact on your organization’s insider risk posture.
To get started, visit the Code42 Incydr app page.
