Managing Insider Risk takes an ecosystem
Today we are excited to announce that Code42 is now a member of the CyberArk C3 Alliance. CyberArk’s C3 Alliance, its global technology partner program, is comprised of forward-thinking security and IT technology organizations. It is committed to integrating best of breed solutions that work together to minimize attack surface vulnerabilities and maximize the ability to deter and respond to attacks while keeping operations running smoothly and efficiently.
Joining the program also marks Code42’s first Privileged Access Management (PAM) integration. This integration with CyberArk enhances Code42’s Insider Risk Management (IRM) framework from an ecosystem perspective. An ecosystem approach that brings together best-of-breed cybersecurity market leaders and one that is customer-centric is an imperative in solving today’s greatest cybersecurity challenges. This customer-centricity is at the heart of Code42’s technology partner ecosystem and is built in alignment with the IRM framework.
The IRM framework provides an outline for the people, process and technology capabilities needed in order to answer the five most essential questions in data security today. Simply put, security leaders need to know:
- Where is my data at risk?
- What data risk matters?
- When should my team be alerted?
- How should we respond?
- Why does this matter?

Security leaders who can easily answer these questions have found IRM solutions that provide context, build cross functional alignment, increase intelligence, and enable response to ultimately optimize corporate risk posture.
Privileged users typically have the ‘keys to the kingdom’ that can unlock corporate secrets and sensitive corporate data. Privilege misuse could be a result of either a negligent or a malicious user with privileged access. Integrating with PAM solutions and leveraging information about privileged users as part of a holistic IRM solution helps to identify when valuable data is exposed by individuals with privileged access. This context informs the right-sized response control needed, and triggers PAM technologies to contain detected data leaks by revoking privileged access credentials. Together, Code42 Incydr and CyberArk do exactly this through Incydr Flows. The outcome is more context and stronger response controls to manage Insider Risk.
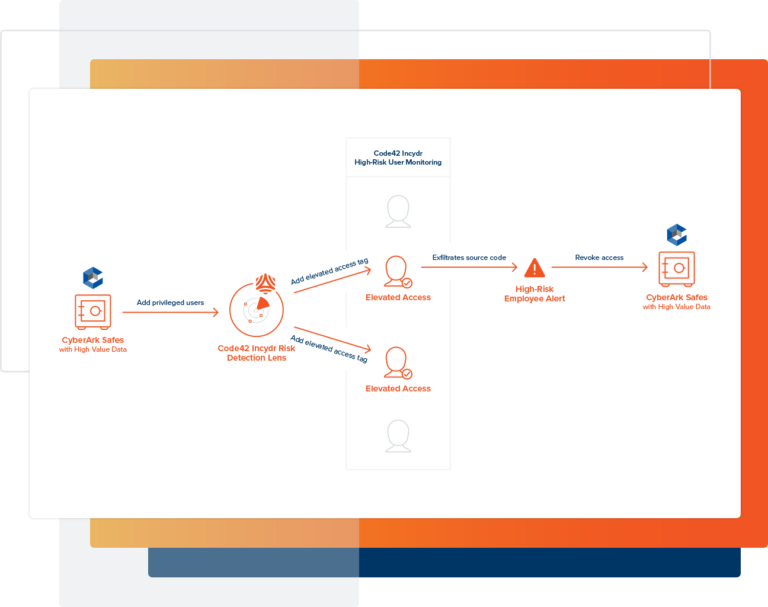
Incydr + CyberArk Flow
Users with privileged access credentials have access to sensitive systems and applications that can contain production data and very sensitive IP. When corporate data is leaked (regardless of the intent), it impacts corporate finances, reputation and competitive standing. That’s why security teams need to respond to data leaks caused by user groups with privileged access differently than they manage other user groups.
The Incydr + CyberArk Flow is a no-code automated integration, powered by Workato, that mitigates Insider Risk caused by individuals with privileged access. It helps security teams:
- Simplify processes that rely on disparate systems and multiple teams
- Accelerate response times
- Reduce manual, repetitive or error prone tasks
How it works
- CyberArk populates Incydr’s High Risk Lens with a list of employees who have access to the company’s most sensitive safes.
- Incydr groups these users in a “elevated access” user group
- A user in this user risk group exfiltrates source code
- Incydr triggers an alert with an IRI with context that source code exfiltration has occurred
- CyberArk disables the users elevated credentials

See for yourself
The Incydr Flow automates actions based on triggers between Incydr and CyberArk. Watch this demo video to see for yourself.
Want to learn more about other automated integrations like the Incydr + CyberArk Flow? Check out this web page for more information about all available Incydr Flows or contact us.