MANUFACTURING
Your Blueprint for Comprehensive Data Protection
Code42 Incydr™ provides complete visibility into data leak and theft without any complex policies – so you can keep critical IP like CAD designs, machine data, and production data securely where it belongs.

Lack of visibility into file movement
is a data governance problem
You know more than anyone the importance of protecting sensitive data from leaving your organization – product designs, manufacturing process details and more. But traditional policy-based approaches freeze productivity and miss the most common ways data is exfiltrated today – via personal email and consumer versions of business applications.
How Incydr Works
Why manufacturing companies
need Insider Risk Management
Protect product designs and your competitive advantage
New and incremental product development takes several years, so it is critical to protect intellectual capital from leaking to competitors who could get to market first. But to protect that data, you need to know where and how it’s exposed.
Get to market quickly and securely
When you lose critical information–whether it’s leaked or negligently misused–you’re delaying a process that already takes years. To protect that fragile value chain, you need to have processes and plans in place to protect data–and the right controls active to respond quickly when data is put at risk.
Protect customer confidence and stay compliant
When intellectual property is lost it often requires disclosures and makes headlines, which harm public perception and consumer confidence. Incydr helps you widen your compliance lens and ensure you have visibility and context into the behaviors that leave you most exposed.
How Incydr protects IP from breaches and misuse
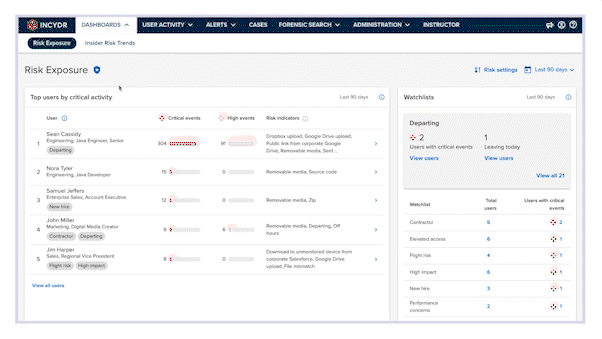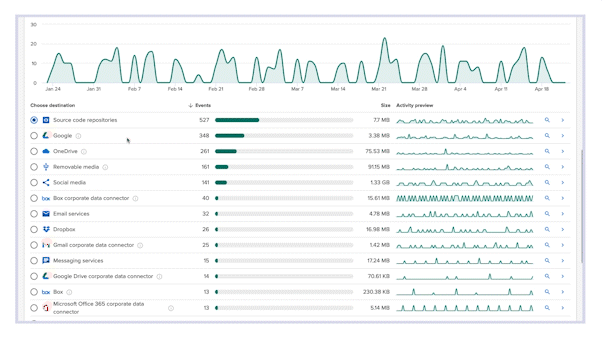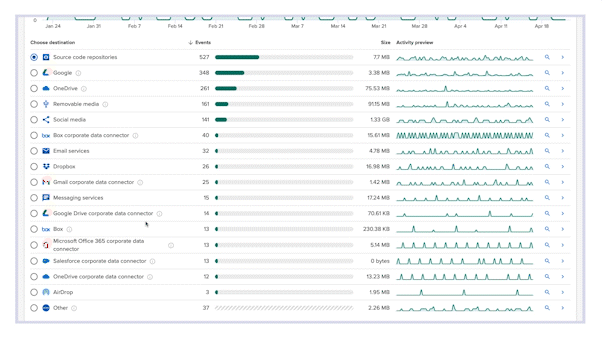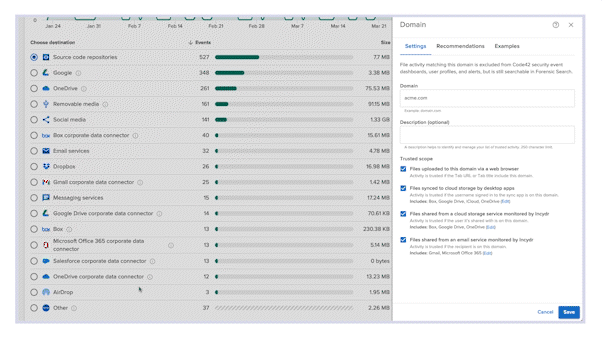
Visibility into all file movement
Incydr gives you a clear understanding of your risk exposure across the value chain, which starts by monitoring the places IP lives (like computers and corporate cloud apps like O365 email and OneDrive), while exfiltration detectors identify files that move to a place or person you don’t trust.
Provides context to data exfiltrations
Incydr enables you to review only the risky behavior that really matters with a prioritized understanding of all data exposure. You’ll be able to confidently respond with a wide range of controls that suit the situation.
Improves data risk posture
Without the need to develop new policies and procedures, you’ll gain control over the data leaving your organization and decrease how often employees put data at risk in the future.

Hear what our manufacturing customers have to say
“Incydr helps us catch risky data movement and take action. HR, legal and managers appreciate the capabilities that the security team has — and that allows them to be a partner in corporate data loss initiatives.”
David Chiang, IT Systems Engineer at MACOM
Want to see Incydr from the inside?
In under four minutes, our product demo shows how Incydr can see and stop data leaks – before major damage is done.
Watch Demo Now